Wannacry之t.wnry核心库解密算法完全分析
已经发布于freebuf : http://www.freebuf.com/column/135103.html
Wannacry机理很多安全厂商都已经分析透了,他的加密核心功能就在他释放的t.wrny这个文件里,这个文件实际上是个动态链接库,是被Wanncry通过他自己的RSA+AES加密存放的,Wannacry在释放的时候会先读取到内存,然后通过RSA还原AES的key密码,最后通过AES解密程序解密到内存来加载动态库,该算法和Wannacry的文件加解密算法是一样的,下面我们就来具体分析该文件是如何解密的。
Wannacry是在taskchs.exe的入口函数里进行解密,我们来看下:
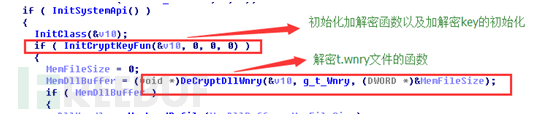
注意两个特别标注的函数InitCryptKeyFun和DeCryptDllWnry,前者是为解密而初始化一些加密函数的初始化和RSA public库的导入,后者是解密的函数,
1. InitCryptKeyFun
首先来分析InitCryptKeyFun
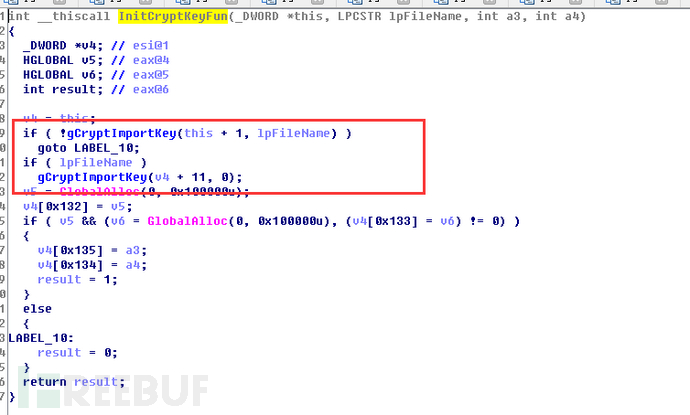
首选会调用CryptImportKey去导入key,再继续进入CryptImportKey函数
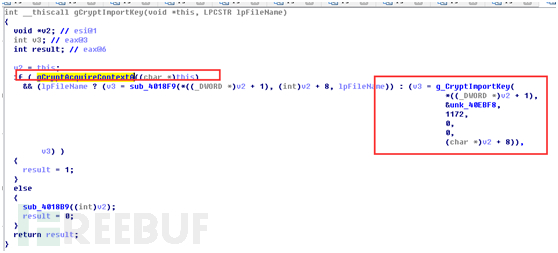
开始先获取加密的上下文,然后在导入key,在跟进CryptAcquireContextA
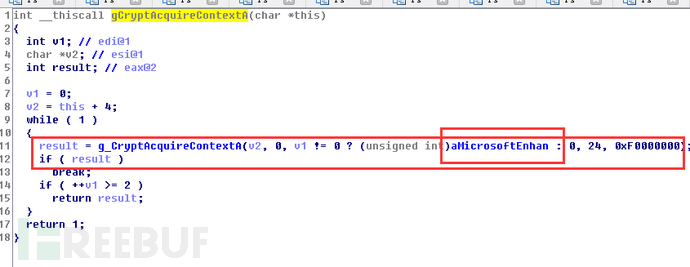
这里终于看到了创建的完整代码了,其中aMicrosoftEnhan = “Microsoft Enhanced RSA and AES Cryptographic Provider”,那么这里的创建获取Context写成代码就是
CryptAcquireContext(&m_HCRYPTPROV,0,"Microsoft Enhanced RSA and AES Cryptographic Provider",PROV_RSA_AES,CRYPT_VERIFYCONTEXT)
我们再继续返回分析g_CryptImportKey函数的导入代码,上图中的unk_40EBF8地址是Wannacry内置在.data节的一个public key,大小1172个字节:
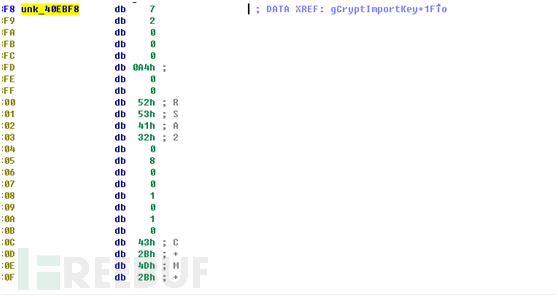
那么我们就可以写成代码是
CryptImportKey(m_HCRYPTPROV,unk_40EBF8,1172,0,0,&m_HCRYPTKEY)
自此初始化key的步骤已经结束,在InitCryptKeyFun的最后还有两个分配GlobalAlloc分配0×100000大小的内存的步骤,这个是为了后续解密用的缓冲区,至此Wannacry初始化De Crypt的过程结束,我们可以写代码。
class CCryptFile
{
public:CCryptFile(void);virtual ~CCryptFile(void);HCRYPTPROV m_HCRYPTPROV;HCRYPTKEY m_HCRYPTKEY;HGLOBAL m_Global_0;//全局堆1BYTE* m_Global_1;//全局堆2
public:BOOL InitKey();PVOID DeCryptWnry( LPCTSTR FilePath ,DWORD& FileMemSize );BOOL DeCryptPrivateKey( PVOID InBuffer,DWORD InSize,BYTE* OutBuffer,DWORD* OutSize);
};
BYTE g_byRsaData[1173] = {
0x7 ,0x2 ,0x0 ,0x0 ,0x0 ,0xA4 ,0x0 ,0,'R','S','A','2',0x0,0x8,0x0,0x0,0x1,0x0,0x1,0x0,
0x43 ,0x2B ,0x4D ,0x2B ,0x4 ,0x9C ,0x0A ,0xD9,0x9F,0x1E,0xDA,0x5F ,0xED ,0x32 ,0xA9 ,0xEF ,0xE1 ,0xCE,
0x1A ,0x50 ,0xF4 ,0x15 ,0xE7 ,0x51 ,0x7B ,0xEC ,0xB0 ,0x27 ,0x56 ,0x05 ,0x58 ,0xB4 ,0xF6 ,0x83,
0xC9 ,0xB6 ,0x77 ,0x5B ,0x80 ,0x61 ,0x18 ,0x1C ,0xAB ,0x14 ,0xD5 ,0x6A ,0xFD ,0x3B ,0x70 ,0x9D ,
0x13 ,0x3F ,0x2E ,0x21 ,0x13 ,0xF1 ,0xE7 ,0xAF ,0xE3 ,0xFB ,0xAB ,0x6E ,0x43 ,0x71 ,0x25 ,0x6D ,
0x1D ,0x52 ,0xD6 ,0x05 ,0x5F ,0x13 ,0x27 ,0x9E ,0x28 ,0x89 ,0xF6 ,0xCA ,0x90 ,0x93 ,0x0A ,0x68 ,
0xC4 ,0xDE ,0x82 ,0x9B ,0xAA ,0xC2 ,0x82 ,0x02 ,0xB1 ,0x18 ,0x60 ,0x01 ,0x63 ,0x1B ,0xBC ,0x71 ,
0x8D ,0xBE ,0x64 ,0x88 ,0x5E ,0xD5 ,0x0D ,0x6C ,0xC1 ,0x9C ,0xC9 ,0x01 ,0x36 ,0x89 ,0xC9 ,0x80 ,
0x37 ,0x8F ,0x1D ,0x89 ,0x67 ,0x4F ,0x0C ,0xB1 ,0x3C ,0x61 ,0x09 ,0x3A ,0x02 ,0x5D ,0xB8 ,0x4E ,
0xF5 ,0x88 ,0x0A ,0x9F ,0x8C ,0x0A ,0x86 ,0xDF ,0x91 ,0xFE ,0xCD ,0x9F ,0xA3 ,0xA0 ,0x13 ,0xD3 ,
0x2D ,0x30 ,0x77 ,0xD1 ,0xF0 ,0xA8 ,0xD7 ,0xAB ,0x96 ,0xE5 ,0x48 ,0x96 ,0x37 ,0x03 ,0x69 ,0x64 ,
0x97 ,0x06 ,0x5C ,0x27 ,0x50 ,0x8C ,0x91 ,
0x76 ,0x67 ,0x85 ,0x3A ,0x6C ,0x6A ,0xB2 ,0x59 ,0x12 ,0x0A ,0x61 ,0xF2 ,0xA1 ,0xEE ,0xA8 ,0x24 ,
0xC8 ,0xE4 ,0xB1 ,0x11 ,0x6D ,0xD6 ,0xCC ,0xF7 ,0x8F ,0x4C ,0x5E ,0xB0 ,0x55 ,0x84 ,0x81 ,0x6D ,
0x60 ,0x45 ,0x84 ,0x0F ,0xFC ,0xDF ,0xF9 ,0x27 ,0xA5 ,0x52 ,0xC9 ,0x5B ,0x06 ,0x28 ,0xA3 ,0xDE ,
0x74 ,0x03 ,0xD6 ,0xC7 ,0x72 ,0x66 ,0xDC ,0xBE ,0xA4 ,0x1E ,0xFF ,0x20 ,0x96 ,0xED ,0x51 ,0x84 ,
0x00 ,0xCC ,0x9C ,0x36 ,0x64 ,0xF2 ,0x85 ,0x4D ,0xCF ,0x36 ,0x60 ,0xDD ,0xC8 ,0xB0 ,0xF1 ,0x91 ,
0xDB ,0x7A ,0x0B ,0x83 ,0xEE ,0xCF ,0xEF ,0x19 ,0xD7 ,0x12 ,0xDA ,0xAE ,0x86 ,0xD9 ,0xF9 ,0x0E ,
0xBE ,0x02 ,0xAF ,0x78 ,0xF3 ,0x5B ,0x49 ,0xBE ,0x0C ,0x98 ,0xAF ,0xB5 ,0x5F ,0xD6 ,0x8A ,0x4C ,
0x05 ,0x48 ,0x64 ,0x9C ,0x40 ,0xE1 ,0x1C ,0xF9 ,0x3C ,0xC4 ,0xE4 ,0x42 ,0x08 ,0x2D ,0xB2 ,0xB8 ,
0x8A ,0xE6 ,0x0B ,0x6D ,0xDF ,0x93 ,0xCC ,0x34 ,0xE8 ,0x48 ,0x30 ,0x93 ,0x5D ,0xDF ,0x8D ,0x2E ,
0xB3 ,0x3D ,0x35 ,0xE4 ,0x66 ,0x30 ,0xAD ,0x8B ,0xE7 ,0x20 ,0x3D ,0xE0 ,0xC9 ,0xD9 ,0x6C ,0x36 ,
0x4B ,0x79 ,0xB9 ,0x64 ,0xCD ,0xBC ,0x5E ,0x24 ,0x48 ,0xD4 ,0x88 ,0x90 ,0x1C ,0x3D ,0x17 ,0x4E ,
0x65 ,0x0C ,0xEC ,0xFB ,0x1B ,0x2B ,0xEC ,0x5C ,0xC3 ,0x06 ,0xD6 ,0x6C ,0x39 ,0xD8 ,0x6C ,0x7E ,
0x23 ,0x9F ,0x40 ,0xAF ,0x40 ,0x61 ,0xB4 ,0xFB ,0xB1 ,0xF6 ,0x82 ,0xCD ,0xA1 ,0x26 ,0xB8 ,0x8D ,
0xC8 ,0x38 ,0x8F ,0x94 ,0x03 ,0x4E ,0xFB ,0xBB ,0xEC ,0x17 ,0x5E ,0xDD ,0x46 ,0xF7 ,0xE7 ,0xFB ,
0xDF ,0x25 ,0x21 ,0xAD ,0x35 ,0xBD ,0x9B ,0x1D ,0xB5 ,0x01 ,0x3F ,0x4E ,0xB0 ,0x20 ,0xB7 ,0x23 ,
0x36 ,0x79 ,0x81 ,0x29 ,0x3C ,0xDE ,0xE2 ,0x76 ,0xD7 ,0xE6 ,0x1F ,0x9F ,0xEA ,0x2D ,0xA5 ,0xC4 ,
0x6A ,0xAA ,0x40 ,0x30 ,0x0D ,0xCC ,0xFE ,0x58 ,0xE9 ,0x89 ,0x28 ,0xCB ,0xD7 ,0xE4 ,0x9C ,0x7B ,
0xB9 ,0x50 ,0x17 ,0xA7 ,0x31 ,0x21 ,0x3B ,0xB4 ,0x91 ,0xF3 ,0x84 ,0xA6 ,0xBD ,0x9E ,0x03 ,0xCA ,
0xE9 ,0xCD ,0xEE ,0x4D ,0x2B ,0x29 ,0xFA ,0x02 ,0x0F ,0xE7 ,0x2C ,0xAE ,0x30 ,0xBD ,0x85 ,0xCC ,
0x2D ,0x13 ,0x83 ,0x12 ,0x53 ,0xD3 ,0xF3 ,0x41 ,0x4E ,0xF5 ,0x23 ,0xD6 ,0xCE ,0x5F ,0x41 ,0xCD ,
0x81 ,0x7C ,0x3B ,0xF0 ,0x49 ,0x81 ,0xB8 ,0xEE ,0x8D ,0x35 ,0x3C ,0xBA ,0xEC ,0x92 ,0xC7 ,0xEE ,
0xCF ,0x24 ,0x63 ,0x01 ,0xF3 ,0x4A ,0xF4 ,0xD9 ,0xDA ,0x8B ,0xE2 ,0xC0 ,0xA4 ,0xA5 ,0x7F ,0xDA ,
0x8F ,0x3C ,0x50 ,0x19 ,0xEC ,0xC2 ,0x33 ,0x5A ,0x8F ,0xEE ,0x7B ,0x5A ,0xE9 ,0x83 ,0x7A ,0x96 ,
0xFD ,0x94 ,0x4B ,0x69 ,0x50 ,0x9A ,0xD2 ,0x34 ,0xD1 ,0x09 ,0x61 ,0x45 ,0x96 ,0x7D ,0xD8 ,0x12 ,
0x5E ,0xA8 ,0xAE ,0x7A ,0xC0 ,0x26 ,0xA5 ,0x6F ,0xD6 ,0xE5 ,0x64 ,0x93 ,0x03 ,0x13 ,0xA3 ,0x29 ,
0x6D ,0x03 ,0x24 ,0xF7 ,0xC2 ,0x89 ,0xE9 ,0x46 ,0x46 ,0x72 ,0xAB ,0x54 ,0xDC ,0xD8 ,0xC7 ,0x75 ,
0x0F ,0x2D ,0x13 ,0x31 ,0xE7 ,0x6D ,0x88 ,0xA1 ,0x3E ,0xA1 ,0x2D ,0xBE ,0xFF ,0xDB ,0x94 ,0xD1 ,
0xBD ,0x6D ,0xE3 ,0xC2 ,0x55 ,0xC7 ,0xCA ,0xFB ,0x2B ,0x63 ,0x31 ,0x17 ,0x97 ,0x42 ,0x91 ,0x93 ,
0x21 ,0xDD ,0x53 ,0x25 ,0x1D ,0x64 ,0xC9 ,0x95 ,0x64 ,0xD9 ,0xB5 ,0x7A ,0x9F ,0xA3 ,0xCA ,0xE2 ,
0x0F ,0x19 ,0x66 ,0xE4 ,0x04 ,0xB5 ,0x4D ,0x6F ,0x5D ,0x33 ,0x76 ,0x1C ,0xE9 ,0x20 ,0x71 ,0x4B ,
0x22 ,0xE0 ,0x55 ,0x5E ,0x91 ,0x56 ,0x54 ,0x94 ,0x3C ,0x36 ,0x3B ,0xFD ,0xFE ,0xA1 ,0x62 ,0xD0 ,
0xDF ,0xD3 ,0x6E ,0x95 ,0x8B ,0xE1 ,0x96 ,0xCE ,0x4F ,0x7C ,0x78 ,0x38 ,0x2B ,0x5E ,0x5F ,0x1B,
0x8C ,0x93 ,0x80 ,0x5A ,0x6D ,0x23 ,0x6F ,0x6D ,0xF7 ,0x19 ,0x88 ,0xF1 ,0x8C ,0x3D ,0x52 ,0x1B ,
0xD8 ,0xAB ,0xB4 ,0xD4 ,0xA0 ,0x88 ,0x0D ,0xAC ,0xFB ,0x7A ,0xFA ,0xC2 ,0x35 ,0xC4 ,0xA7 ,0xA9 ,
0x50 ,0x62 ,0x4A ,0xAC ,0x98 ,0x9B ,0x30 ,0xE1 ,0x59 ,0x37 ,0x51 ,0x0C ,0x6D ,0x28 ,0x74 ,0xAC ,
0x11 ,0xD9 ,0x70 ,0x38 ,0x2C ,0x35 ,0xD3 ,0xB8 ,0xD9 ,0xF1 ,0xB7 ,0x4F ,0xA1 ,0x34 ,0x36 ,0x8B ,
0x29 ,0x61 ,0x39 ,0x35,0x00 ,0x70 ,0xDE ,0x73 ,0xE5 ,0xD5 ,0x1C ,0xBB ,0x5E ,0xB8 ,0x60 ,0xB6 ,
0x70 ,0x49 ,0x85 ,0x79 ,0x65 ,0x46 ,0x7A ,0x94 ,0x81 ,0xD6 ,0xCC ,0x12 ,0x05 ,0x84 ,0x43 ,0x40,
0x6D ,0xFC ,0x77 ,0x55 ,0x8E ,0x45 ,0xF8 ,0x3D ,0xB9 ,0x87 ,0xA7 ,0x89 ,0xD2 ,0x59 ,0x28 ,0xCE ,
0x16 ,0x9A ,0x53 ,0xDC ,0x9D ,0x82 ,0x93 ,0xAD ,0xB1 ,0x3C ,0xB9 ,0xA6 ,0x2D ,0xAA ,0x9D ,0x43,
0xEC ,0xE2 ,0x7D ,0xCA ,0x32 ,0x2F ,0x4F ,0x2D ,0x5F ,0x2E ,0x58 ,0x38 ,0x77 ,0x2E ,0x2B ,0x1B ,
0x0A ,0xFA ,0xFE ,0x79 ,0x5A ,0x80 ,0xE1 ,0x8D ,0x23 ,0x67 ,0x40 ,0xFF ,0xD3 ,0xD3 ,0x95 ,0x7A ,
0x14 ,0xBE ,0x93 ,0x1B ,0xF8 ,0xEF ,0x37 ,0xC2 ,0xEE ,0xC8 ,0xBF ,0x59 ,0x3C ,0x9C ,0x5D ,0x25 ,
0xB6 ,0x44 ,0xFF ,0x6B ,0x9B ,0xE9 ,0xB4 ,0xFD ,0x59 ,0x85 ,0xBA ,0xF1 ,0x3A ,0x01 ,0x05 ,0xF1 ,
0x3E ,0x62 ,0x0D ,0x7F ,0x1F ,0xE2 ,0x81 ,0x97 ,0x66 ,0x63 ,0x90 ,0x20 ,0xBB ,0x96 ,0xB4 ,0xCF ,
0x44 ,0xC7 ,0x7C ,0x7E ,0x7D ,0x25 ,0x2E ,0x31 ,0x35 ,0x8B ,0x2A ,0x18 ,0xAB ,0xD2 ,0x41 ,0xC9 ,
0x32 ,0xAA ,0x4B ,0xCA ,0xEF ,0x28 ,0x1D ,0xBF ,0x2A ,0x9C ,0x1C ,0x36 ,0x02 ,0x6B ,0x02 ,0x0F ,
0xA7 ,0xED ,0x10 ,0xC0 ,0xA0 ,0xDA ,0xCF ,0x09 ,0x72 ,0x59 ,0x5B ,0xC6 ,0x3C ,0xF9 ,0x15 ,0x7F ,
0xAA ,0x22 ,0x00 ,0x72 ,0xE0 ,0xA5 ,0x5C ,0x79 ,0x06 ,0x6E ,0x62 ,0x35 ,0x33 ,0x89 ,0x56 ,0xAB ,
0x5F ,0xF1 ,0xFD ,0x93 ,0x62 ,0x4E ,0x81 ,0x1E ,0x3D ,0xFC ,0x05 ,0x69 ,0xA4 ,0x2F ,0x51 ,0x1B ,
0xE2 ,0xC8 ,0x0E ,0xA6 ,0x86 ,0xA2 ,0xBF ,0x9D ,0xA4 ,0x9C ,0xB3 ,0xDC ,0x89 ,0xB3 ,0xE3 ,0xB0 ,
0xF0 ,0xD7 ,0x60 ,0xD6 ,0x6C ,0xDE ,0x69 ,0x1E ,0xC9 ,0xB0 ,0x02 ,0x85 ,0x96 ,0xD7 ,0x35, 0x86 ,
0x36 ,0x16 ,0x5B ,0xE6 ,0x05 ,0xE1 ,0xF9 ,0x0B ,0xED ,0x25 ,0x80 ,0xE0 ,0x0A ,0x04 ,0xC5 ,0x96 ,
0x5D, 0x34 ,0x6C ,0x4C ,0xF0 ,0xE0 ,0xC7 ,0xB7 ,0x8A ,0x90 ,0x3C ,0x98 ,0xA2 ,0x7A ,0x92 ,0xEA ,
0x51 ,0xE9 ,0x05 ,0xEC ,0x7D ,0x3C ,0xC9 ,0xCD ,0xAA ,0xB6 ,0x66 ,0xB3 ,0xDB ,0x48 ,0xCF ,0x7D ,
0xFB ,0x6D ,0xDD ,0x04 ,0xB9 ,0x1B ,0x97 ,0x9E ,0xBE ,0xE1 ,0x58 ,0x66 ,0xFD ,0xE9 ,0x70 ,0xAC ,
0xF9 ,0xFF ,0xB6 ,0x23 ,0x17 ,0xFD ,0xF0 ,0x35 ,0x0C ,0x41 ,0x3A ,0x38 ,0x9A ,0x2F ,0x3F ,0x16 ,
0x2A ,0xE8 ,0xA9 ,0x73 ,0x30 ,0x7C ,0x38 ,0xC9 ,0xC4 ,0x7E ,0xC6 ,0x68 ,0xA4 ,0x78 ,0xFE ,0x6D ,
0x00 ,0x28 ,0x4E ,0x33 ,0x87 ,0xE5 ,0xB6 ,0xC9 ,0xC5 ,0x3D ,0xEC ,0x0E ,0x92 ,0x03 ,0xEB ,0x15 ,
0x9B ,0x38 ,0x73 ,0xBF ,0x0F ,0xC1 ,0x7B ,0x5A ,0x89 ,0x51 ,0xF1 ,0x97 ,0x71 ,0xF5 ,0xD5 ,0xCA,
0x44 ,0x9F ,0x87 ,0xE7 ,0xDD ,0x35 ,0x6D ,0xC0 ,0x1F ,0xCD ,0x5B ,0x93 ,0xC1 ,0x00 ,0x0E ,0xF1 ,
0xA9 ,0x25 ,0xC8 ,0xF6 ,0xE8 ,0x8B ,0xC7,0 //4D
};
BOOL CCryptFile::InitKey()
{if(CryptAcquireContext(&m_HCRYPTPROV,0,"Microsoft Enhanced RSA and AES Cryptographic Provider",PROV_RSA_AES,CRYPT_VERIFYCONTEXT)){if(CryptImportKey(m_HCRYPTPROV,g_byRsaData,1172,0,0,&m_HCRYPTKEY)){m_Global_0 = GlobalAlloc(0, 0x100000);if ( m_Global_0 ){m_Global_1 = (BYTE*)GlobalAlloc(0, 0x100000);if ( m_Global_1 ){return TRUE;}}}}return FALSE;
}
2. DeCryptDllWnry
进入DeCryDllWnry函数
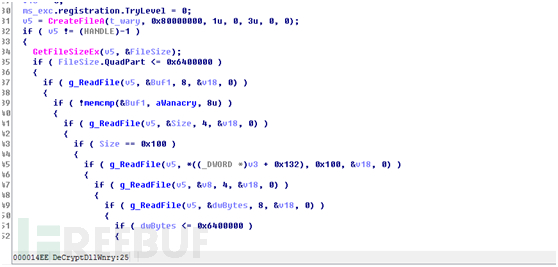
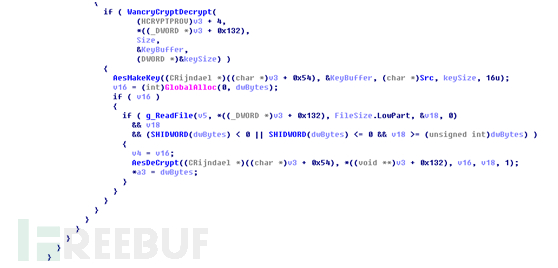
该函数的前面都是一些文件读写函数,是读取文件头,文件头大小4K,前8个字节是加密文件标识付”WANACRY!”,接着读取4个字节是密钥大小,这个size值大小是固定大小0×100,然后开始读取密钥数据,读完再读取4个字节,这个值是文件加密类型目前这个值为4,再继续读取8个字节,这个值是原始文件的长度,Wannacry规定了文件要小于0×6400000,以上都满足了然后就开始进入WancryCryptDecrypt函数
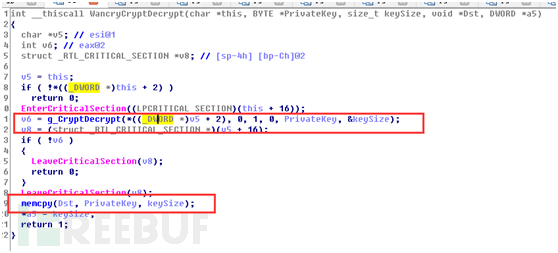
这个函数很简单就是使用CryptDecrypt解密之前读取的文件中密钥得到真实AES密钥,代码如下
BOOL CCryptFile::DeCryptPrivateKey(
PVOID InBuffer,
DWORD InSize,
BYTE* OutBuffer,
DWORD* OutSize)
{
if ( m_HCRYPTPROV && m_HCRYPTKEY && InBuffer && InSize)
{
DWORD BufferSize = InSize;
if(CryptDecrypt(
m_HCRYPTKEY,
0,
TRUE,
0,
(BYTE *)InBuffer,
&BufferSize
))
{
memcpy(OutBuffer,InBuffer,BufferSize);
*OutSize = BufferSize;
return TRUE;
}
}
return FALSE;
}
WancryCryptDecrypt函数返回后就开始进入了AesMakeKey函数,这个函数的作用是对真实密钥进行扩展操作,根据算法位数进行相应的扩展。
首先根据key的大小来计算轮询的次数
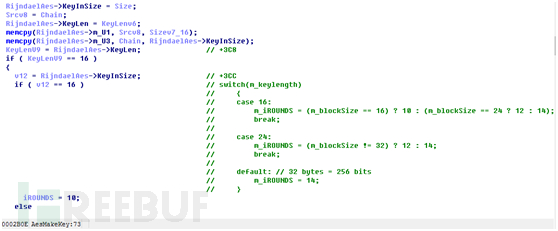
接着初始化ke kd数组的数据
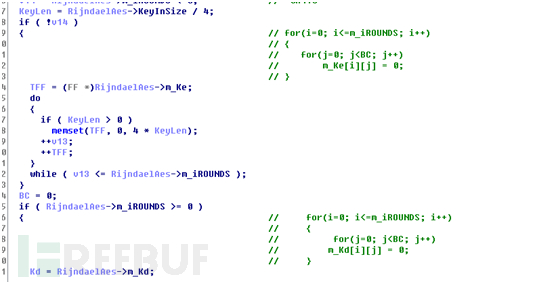
接着初始化tk数组的数据
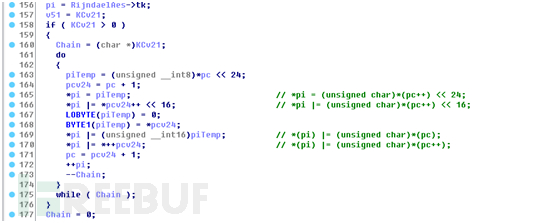
然后就开始轮询填充计算扩展key数据
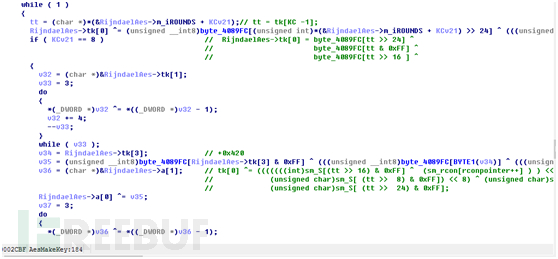
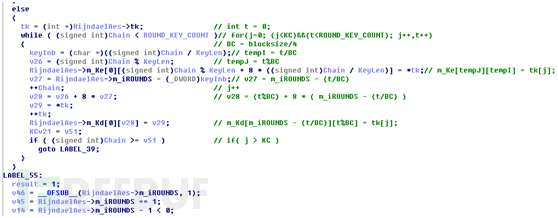
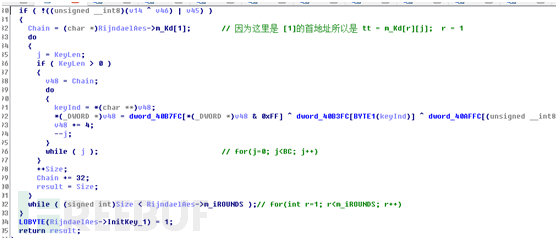
计算结束后就返回true,并把InitKey_1填1,表示key已经被扩展,key扩展结束后就进入正式的解密函数
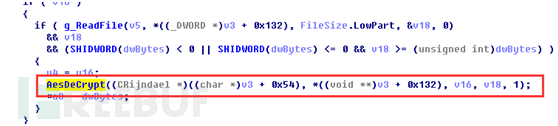
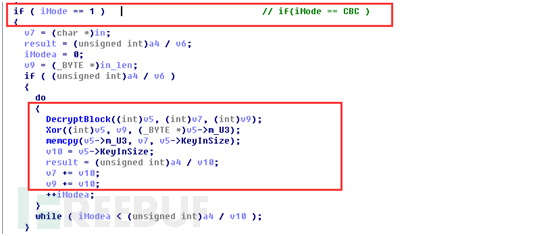
我们可以看到该函数最后一个参数是1,这个值是1就是表示使用CBC(分组密码链)方式解密,然后就调用DecryptBlock解密,解密的结果copy到缓冲区,代码如下:
PVOID CCryptFile::DeCryptWnry( LPCTSTR FilePath ,DWORD& FileMemSize )
{
char ReadBuffer[200] = {0};
DWORD ReadSize = 0;
DWORD AesCryptSize = 0;
DWORD CryptFileSize = 0;
LARGE_INTEGER FileSize = {0};
char* FileBuffer = NULL;
if (FilePath)
{
HANDLE hFile = CreateFile(
FilePath,
0x80000000,
1,
0,
3,
0,
0);
if ( hFile != (HANDLE)INVALID_HANDLE_VALUE )
{
GetFileSizeEx(hFile, &FileSize);
if (FileSize.QuadPart && FileSize.QuadPart < 0x6400000i64)
{
if(ReadFile(
hFile,
ReadBuffer,
8,
&ReadSize,
NULL))
{
if ( !memcmp(ReadBuffer,"WANACRY!", 8) )
{
//读取密钥size
if(ReadFile(
hFile,
&AesCryptSize,
4,
&ReadSize,
NULL))
{
if ( AesCryptSize == 0x100 )
{
//读取密钥数据
if(ReadFile(
hFile,
m_Global_0,
0x100,
&ReadSize,
NULL))
{
//读取文件数据大小
if(ReadFile(
hFile,
&CryptFileSize,
4,
&ReadSize,
NULL))
{
//读取文件大小
if(ReadFile(
hFile,
&CryptFileSize,
8,
&ReadSize,
NULL))
{
if (CryptFileSize < 0x6400000 )
{
if(DeCryptPrivateKey(
m_Global_0,
0x100,
(BYTE*)m_Global_1,
&ReadSize))
{
CAESCbC Aes;
if (Aes.MakeKey(
(BYTE*)m_Global_1,
Aes.m_globalChain,
ReadSize,
0x10)) {
FileBuffer = (char*)GlobalAlloc( 0, CryptFileSize + 1 );
if (FileBuffer)
{
memset(
FileBuffer,
0,
CryptFileSize + 1);
if(ReadFile(
hFile,
m_Global_1,
FileSize.LowPart,
&ReadSize,
NULL))
{
Aes.Decrypt( m_Global_1,FileBuffer, ReadSize, 1);
FileMemSize = CryptFileSize;
}
}
}
}
}
}
}
}
}
}
}
}
}
}
}
return FileBuffer;
}
这是代码工程
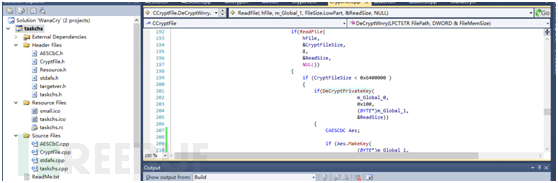
我们来看下效果:
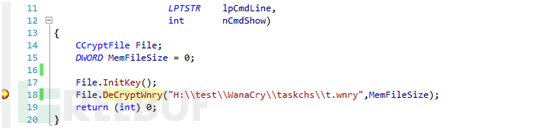
这里是读取文件
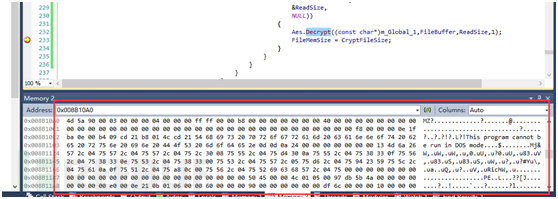
看内存是个pe文件,解密成功。
至此整个算法就分析结束了,Wanncry的AES算法本人暂时不公开,会在后续的文章中公开该算法,而这个解密算法也通用于被Wanncry使用内置配对key加密的文件的解密,本人会在后续推出该工具,而其他被作者专用的私有key加密的文件暂时无法解密,但大家可以多分析下,也许能找到作者的漏洞实现解密,这都需要进行后续的研究去发现。
Wannacry之t.wnry核心库解密算法完全分析相关推荐
- 【Android 安全】DEX 加密 ( Java 工具开发 | 加密解密算法 API | 编译代理 Application 依赖库 | 解压依赖库 aar 文件 )
文章目录 一.加密解密算法 API 二.编译代理 Application 依赖库 三.解压代理 Application 依赖库 aar 文件 参考博客 : [Android 安全]DEX 加密 ( 常 ...
- 加解密算法的概述和总结
加解密算法的概述和总结 一.单向散列算法 也称为Hash(哈希)算法.是一种将任意长度的消息压缩到某一固定长度(消息摘要)的函数(该过程不可逆).Hash函数可用于数字签名.消息的完整性检测.消息起源 ...
- java 实现 DES加密 解密算法
DES算法的入口参数有三个:Key.Data.Mode.其中Key为8个字节共64位,是DES算法的工作密钥:Data也为8个字节64位,是要被加密或被解密的数据:Mode为DES的工作方式,有两种: ...
- 【Android 安全】DEX 加密 ( 代理 Application 开发 | 项目中配置 OpenSSL 开源库 | 使用 OpenSSL 开源库解密 dex 文件 )
文章目录 一.项目中配置 OpenSSL 开源库 二.OpenSSL 开源库解密参考代码 三.解密 dex 文件的 Java 代码 四.解密 dex 文件的 Jni 代码 参考博客 : [Androi ...
- RSA公钥加密与私钥解密算法
首先是随机生成一个密钥对(一个公钥和一个私钥) package com.zy.demo1.secretTest;import lombok.extern.slf4j.Slf4j; import org ...
- 一系列令人敬畏的.NET核心库,工具,框架和软件
内容 一般 框架,库和工具 API 应用框架 应用模板 身份验证和授权 Blockchain 博特 构建自动化 捆绑和缩小 高速缓存 CMS 代码分析和指标 压缩 编译器,管道工和语言 加密 数据库 ...
- GPU/APU加速库、算法及应用
2019独角兽企业重金招聘Python工程师标准>>> 一.开源库源代码优化 1.图像处理相关 2.视频处理与多媒体技术 3.数据加密.压缩与管理 4.网络防御 5.数学库 二.算法 ...
- 六个经典的PHP加密解密算法
六个经典的PHP加密解密算法 六个经典的PHP加密解密算法 非常给力的authcode加密函数,Discuz!经典代码(带详解) 函数authcode($string, $operation, $ke ...
- php三种常用的加密解密算法
给大家介绍php的三种常用的加密解密算法,有一定的参考价值,有需要的朋友可以参考一下,希望对你们有所帮助. 方法一: /*** @param $string 要加密/解密的字符串* @param st ...
最新文章
- poj1220:高精度进制转换模板题
- 吴恩达朋友圈宣布“喜讯”:AI专家王冬岩加入Landing AI...
- 自动驾驶技术-环境感知篇:多传感器融合技术
- mysql重置增量_摆脱困境:在每种测试方法之前重置自动增量列
- java BufferedReader
- POJ 1948 Triangular Pastures (二维01背包)
- 【翻转整数考虑溢出】LeetCode 7. Reverse Integer
- python 初学之环境配置及IED搭建
- sam账号服务器已断开连接,删了sam文件后引发的IIS问题的解决方法
- c语言入门自学免费app,C语言入门学习最新版下载-C语言入门学习app手机版v1.0.2 安卓版-腾飞网...
- lumen php命令,lumen控制器调用artisan
- 普元 AppServer 部署应用时报错:Exception while loading the app : CDI deployment failure
- 【Map】Echarts之iphone销量地图的使用以及详细配置
- Android Studio 在library中引用本地arr的办法
- 台式计算机网线接口松动怎么办,电脑网线接口附近时常有滋滋声是怎么回事
- 端粒效应《The Telemere Effect》程序员的养生指南(二)情绪、思维模式与健康
- NVM Node版本管理工具
- 中国梦之声第二季播出时间
- 按钮角色 role=“button“
- php 如何实现 图表 联动,教你在BDP制作交互式图表实现联动分析
热门文章
- MySQL详细安装和配置图解
- 机器学习分类算法统一指标
- 艾美捷魔力红组织蛋白酶B活性分析试剂盒研究手册
- 创建war包和部署war包,以及实施相关的工具和unix命令
- vCenter 集群EVC设置实例禁用状态 (一)
- 采用scrapy对秀动网演出信息爬取
- Windows Store apps开发[79]Windows 8 开发31日-第21日-摄像头
- 【SonarQube】CentOS7安装SonarQube并集成GitLab-CI实现代码提交后自动扫描
- Discrete_mathematics_with_applications-4th Chapter2 Answer
- BZOJ4554 [Tjoi2016Heoi2016]游戏
